1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
|
0042F998 /. 55 push ebp
0042F999 |. 8BEC mov ebp,esp
0042F99B |. 33C9 xor ecx,ecx ; user32.77D1882A
0042F99D |. 51 push ecx ; user32.77D1882A
0042F99E |. 51 push ecx ; user32.77D1882A
0042F99F |. 51 push ecx ; user32.77D1882A
0042F9A0 |. 51 push ecx ; user32.77D1882A
0042F9A1 |. 51 push ecx ; user32.77D1882A
0042F9A2 |. 51 push ecx ; user32.77D1882A
0042F9A3 |. 53 push ebx
0042F9A4 |. 56 push esi
0042F9A5 |. 8BD8 mov ebx,eax
0042F9A7 |. 33C0 xor eax,eax
0042F9A9 |. 55 push ebp
0042F9AA |. 68 67FB4200 push Acid_bur.0042FB67
0042F9AF |. 64:FF30 push dword ptr fs:[eax]
0042F9B2 |. 64:8920 mov dword ptr fs:[eax],esp
0042F9B5 |. C705 50174300>mov dword ptr ds:[0x431750],0x29
0042F9BF |. 8D55 F0 lea edx,[local.4]
0042F9C2 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9C8 |. E8 8BB0FEFF call Acid_bur.0041AA58
0042F9CD |. 8B45 F0 mov eax,[local.4]
0042F9D0 |. E8 DB40FDFF call Acid_bur.00403AB0
0042F9D5 |. A3 6C174300 mov dword ptr ds:[0x43176C],eax
0042F9DA |. 8D55 F0 lea edx,[local.4]
0042F9DD |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9E3 |. E8 70B0FEFF call Acid_bur.0041AA58
0042F9E8 |. 8B45 F0 mov eax,[local.4]
0042F9EB |. 0FB600 movzx eax,byte ptr ds:[eax]
0042F9EE |. 8BF0 mov esi,eax
0042F9F0 |. C1E6 03 shl esi,0x3
0042F9F3 |. 2BF0 sub esi,eax
0042F9F5 |. 8D55 EC lea edx,[local.5]
0042F9F8 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9FE |. E8 55B0FEFF call Acid_bur.0041AA58
0042FA03 |. 8B45 EC mov eax,[local.5] ; Acid_bur.0042467E
0042FA06 |. 0FB640 01 movzx eax,byte ptr ds:[eax+0x1]
0042FA0A |. C1E0 04 shl eax,0x4
0042FA0D |. 03F0 add esi,eax
0042FA0F |. 8935 54174300 mov dword ptr ds:[0x431754],esi
0042FA15 |. 8D55 F0 lea edx,[local.4]
0042FA18 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA1E |. E8 35B0FEFF call Acid_bur.0041AA58
0042FA23 |. 8B45 F0 mov eax,[local.4]
0042FA26 |. 0FB640 03 movzx eax,byte ptr ds:[eax+0x3]
0042FA2A |. 6BF0 0B imul esi,eax,0xB
0042FA2D |. 8D55 EC lea edx,[local.5]
0042FA30 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA36 |. E8 1DB0FEFF call Acid_bur.0041AA58
0042FA3B |. 8B45 EC mov eax,[local.5] ; 112233
0042FA3E |. 0FB640 02 movzx eax,byte ptr ds:[eax+0x2] ; 取用户名的第三个字符
0042FA42 |. 6BC0 0E imul eax,eax,0xE ; eax = 0x32 * 0xE == 2BC
0042FA45 |. 03F0 add esi,eax
0042FA47 |. 8935 58174300 mov dword ptr ds:[0x431758],esi
0042FA4D |. A1 6C174300 mov eax,dword ptr ds:[0x43176C]
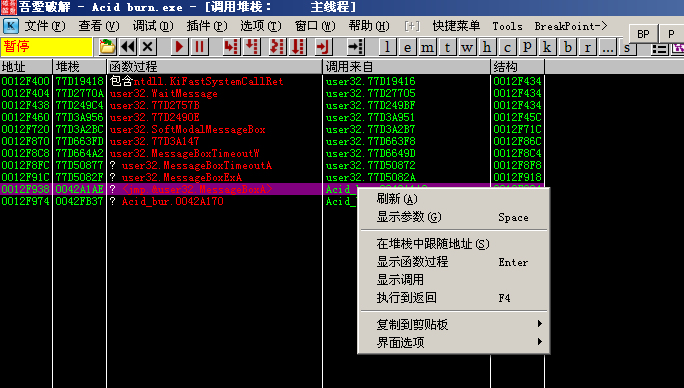
0042FA52 |. E8 D96EFDFF call Acid_bur.00406930 ; 确定tag/serial 是否合格
0042FA57 |. 83F8 04 cmp eax,0x4
0042FA5A 7D 1D jge short Acid_bur.0042FA79
0042FA5C |. 6A 00 push 0x0
0042FA5E |. B9 74FB4200 mov ecx,Acid_bur.0042FB74 ; ASCII 54,"ry Again!"
0042FA63 |. BA 80FB4200 mov edx,Acid_bur.0042FB80 ; ASCII 53,"orry , The serial is incorect !"
0042FA68 |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FA6D |. 8B00 mov eax,dword ptr ds:[eax]
0042FA6F |. E8 FCA6FFFF call Acid_bur.0042A170 ; 弹出错误提示
0042FA74 |. E9 BE000000 jmp Acid_bur.0042FB37
0042FA79 |> 8D55 F0 lea edx,[local.4]
0042FA7C |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA82 |. E8 D1AFFEFF call Acid_bur.0041AA58
0042FA87 |. 8B45 F0 mov eax,[local.4] ; 112233
0042FA8A |. 0FB600 movzx eax,byte ptr ds:[eax] ; 取首字符:0x31
0042FA8D |. F72D 50174300 imul dword ptr ds:[0x431750] ; eax = 0x31 * 0x29 == 0x7D9
0042FA93 |. A3 50174300 mov dword ptr ds:[0x431750],eax
0042FA98 |. A1 50174300 mov eax,dword ptr ds:[0x431750]
0042FA9D |. 0105 50174300 add dword ptr ds:[0x431750],eax
0042FAA3 |. 8D45 FC lea eax,[local.1]
0042FAA6 |. BA ACFB4200 mov edx,Acid_bur.0042FBAC ; CW
0042FAAB |. E8 583CFDFF call Acid_bur.00403708
0042FAB0 |. 8D45 F8 lea eax,[local.2]
0042FAB3 |. BA B8FB4200 mov edx,Acid_bur.0042FBB8
0042FAB8 |. E8 4B3CFDFF call Acid_bur.00403708
0042FABD |. FF75 FC push [local.1] ; CW
0042FAC0 |. 68 C8FB4200 push Acid_bur.0042FBC8 ; UNICODE "-"
0042FAC5 |. 8D55 E8 lea edx,[local.6]
0042FAC8 |. A1 50174300 mov eax,dword ptr ds:[0x431750]
0042FACD |. E8 466CFDFF call Acid_bur.00406718 ; 将16进制转换为十进制字符串:0xFB2 => 4018
0042FAD2 |. FF75 E8 push [local.6] ; 4018
0042FAD5 |. 68 C8FB4200 push Acid_bur.0042FBC8 ; UNICODE "-"
0042FADA |. FF75 F8 push [local.2] ; CRACKED
0042FADD |. 8D45 F4 lea eax,[local.3] ; 返回值
0042FAE0 |. BA 05000000 mov edx,0x5
0042FAE5 |. E8 C23EFDFF call Acid_bur.004039AC
0042FAEA |. 8D55 F0 lea edx,[local.4]
0042FAED |. 8B83 E0010000 mov eax,dword ptr ds:[ebx+0x1E0]
0042FAF3 |. E8 60AFFEFF call Acid_bur.0041AA58
0042FAF8 |. 8B55 F0 mov edx,[local.4] ; 44556677
0042FAFB |. 8B45 F4 mov eax,[local.3] ; CW-4018-CRACKED
0042FAFE |. E8 F93EFDFF call Acid_bur.004039FC ; 比较两个字符串是否相等
0042FB03 75 1A jnz short Acid_bur.0042FB1F ; 关键的跳转
0042FB05 |. 6A 00 push 0x0
0042FB07 |. B9 CCFB4200 mov ecx,Acid_bur.0042FBCC
0042FB0C |. BA D8FB4200 mov edx,Acid_bur.0042FBD8
0042FB11 |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB16 |. 8B00 mov eax,dword ptr ds:[eax]
0042FB18 |. E8 53A6FFFF call Acid_bur.0042A170
0042FB1D |. EB 18 jmp short Acid_bur.0042FB37
0042FB1F |> 6A 00 push 0x0
0042FB21 |. B9 74FB4200 mov ecx,Acid_bur.0042FB74 ; ASCII 54,"ry Again!"
0042FB26 |. BA 80FB4200 mov edx,Acid_bur.0042FB80 ; ASCII 53,"orry , The serial is incorect !"
0042FB2B |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB30 |. 8B00 mov eax,dword ptr ds:[eax]
0042FB32 |. E8 39A6FFFF call Acid_bur.0042A170 ; 弹出错误提示
0042FB37 |> 33C0 xor eax,eax
0042FB39 |. 5A pop edx ; 0012F990
0042FB3A |. 59 pop ecx ; 0012F990
0042FB3B |. 59 pop ecx ; 0012F990
0042FB3C |. 64:8910 mov dword ptr fs:[eax],edx
0042FB3F |. 68 6EFB4200 push Acid_bur.0042FB6E
0042FB44 |> 8D45 E8 lea eax,[local.6]
0042FB47 |. E8 243BFDFF call Acid_bur.00403670
0042FB4C |. 8D45 EC lea eax,[local.5]
0042FB4F |. BA 02000000 mov edx,0x2
0042FB54 |. E8 3B3BFDFF call Acid_bur.00403694
0042FB59 |. 8D45 F4 lea eax,[local.3]
0042FB5C |. BA 03000000 mov edx,0x3
0042FB61 |. E8 2E3BFDFF call Acid_bur.00403694
0042FB66 \. C3 retn
0042FB67 .^ E9 A835FDFF jmp Acid_bur.00403114
0042FB6C .^ EB D6 jmp short Acid_bur.0042FB44
0042FB6E . 5E pop esi ; 0012F990
0042FB6F . 5B pop ebx ; 0012F990
0042FB70 . 8BE5 mov esp,ebp
0042FB72 . 5D pop ebp ; 0012F990
0042FB73 . C3 retn
|